Supporting Error Chains in Static Analysis for Precise Evaluation Results and Enhanced Usability
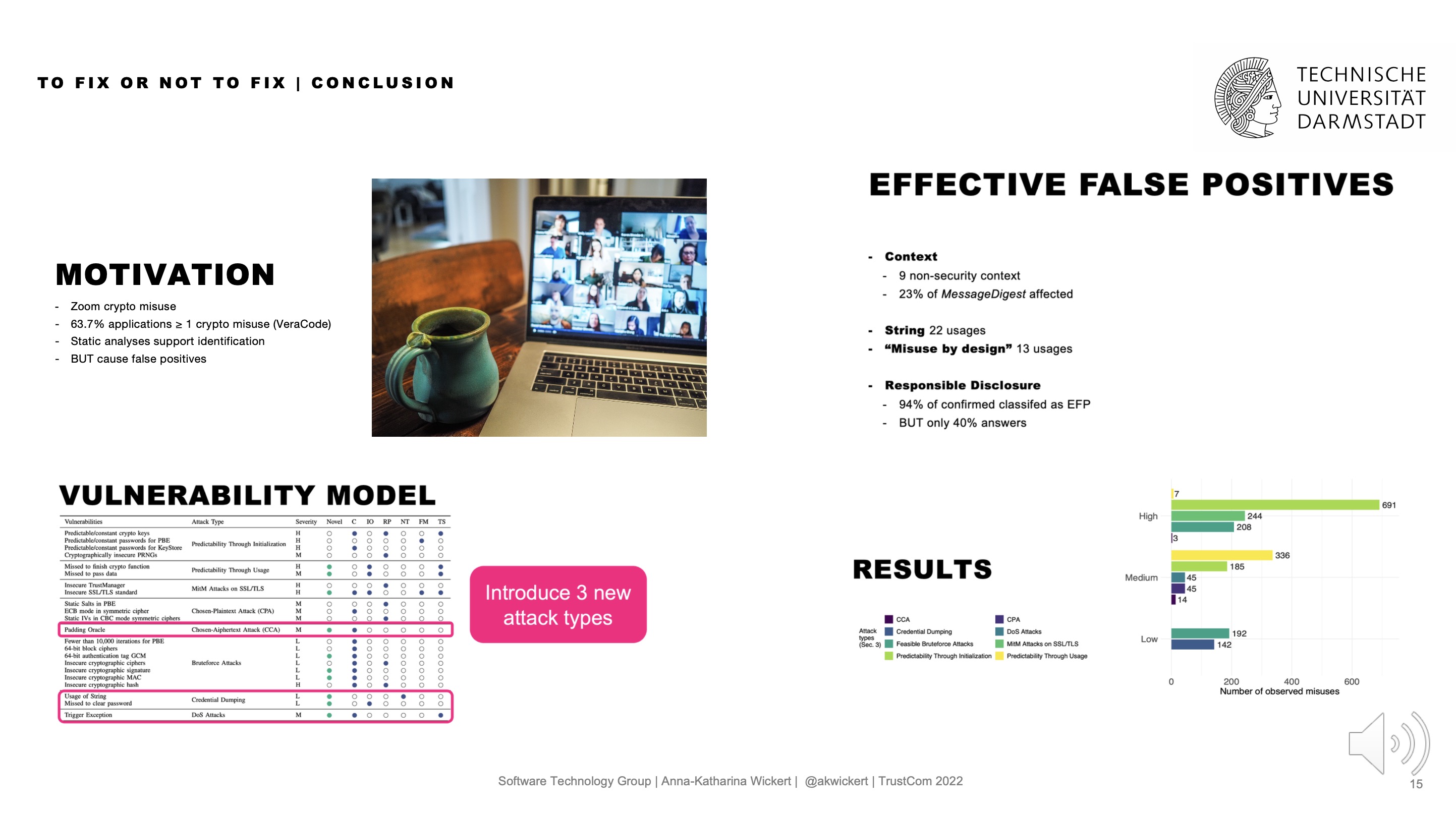
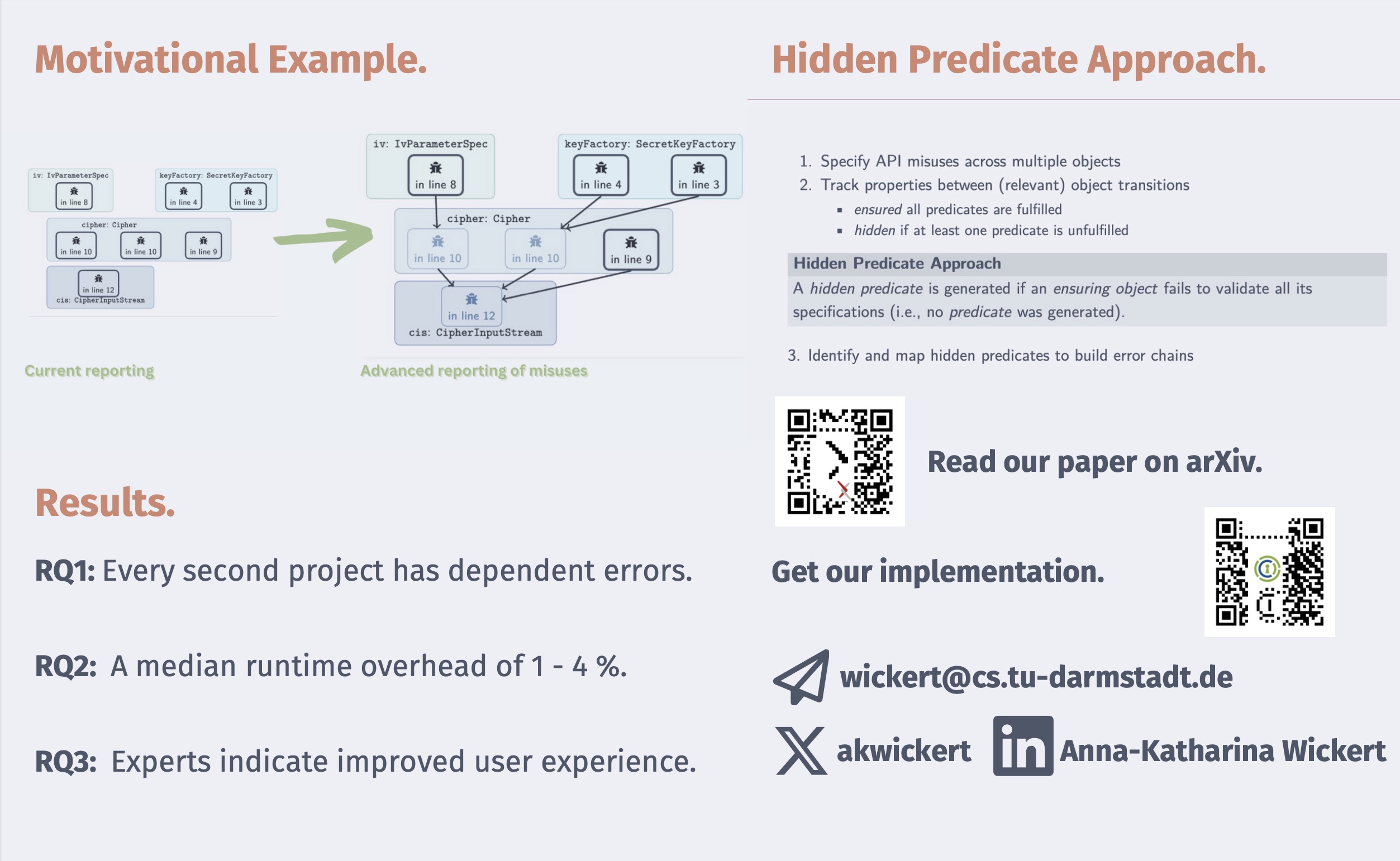
Our paper suggests an adapted algorithm that can report error chains between API misuses. The empirical study onn 471 GitHub repositories showed that 50% of projects are affected by connected cryptographic API misuses. Further, the runtime overhead is minimal, and developers appreciate the adaption.